Oct 12, 2024
MoveBit Discovers and Helps Fix Vulnerability in Sui Cross-Chain Protocol
Sui Vulnerabilities Explanation
Sui[3] is the first Layer 1 blockchain designed from scratch as a permissionless platform. It’s renowned for its scalability, security focus, and rich on-chain assets. Compared to other blockchains, Sui maintains low gas fees even under high network traffic due to its scalability. Move design emphasizes security, mitigating issues like reentrancy vulnerabilities and forged token approvals. By supporting dynamic NFTs and gaming economies, Sui provides a platform for developers to innovate in Web3 development. The Sui Development Kit empowers developers to build applications without constraints, preparing for the arrival of the next billion users.
To expand its ecosystem, Sui incorporates various experimental features such as Native Bridge, zkLogin with Multisig, zkLogin providers, Random beacon, and Enums.

Background
In the evolving landscape of Ethereum’s solo endeavors, major platforms continuously innovate to bolster their capabilities, fostering the development of the DeFi ecosystem. Within this context, various types of non-standard ERC20 tokens have emerged, finding widespread utility within the ecosystem. These tokens include fee-on-transfer tokens, Approval Race Protections tokens, Revert on Zero Value Transfers tokens, Missing Return Values tokens, among others.
Missing Return Values tokens pose a unique challenge due to their deviation from the standard ERC20 protocol. Some tokens, such as USDT, BNB, and OMG, do not return a boolean value on ERC20 methods as required by the ERC20 standard. According to the ERC20 standard, checking the return value is a prerequisite[4]. However, tokens like USDT, which lack return values, can encounter errors when attempting to verify the success of a transfer.
Therefore, special handling is necessary to address this issue.
The vulnerabilities
Funds transferred through the cross-chain bridge using USDT will remain permanently frozen in the protocol
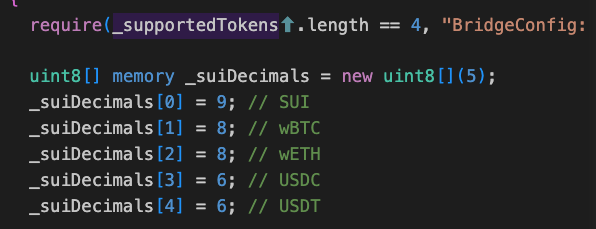
SuiBridge is a cross-chain bridge contract that facilitates users to deposit tokens supported by the protocol and withdraw them on another chain. According to the BridgeConfig contract, we find that the supported tokens include Sui, WBTC, WETH, USDC, USDT, and ETH as shown below.
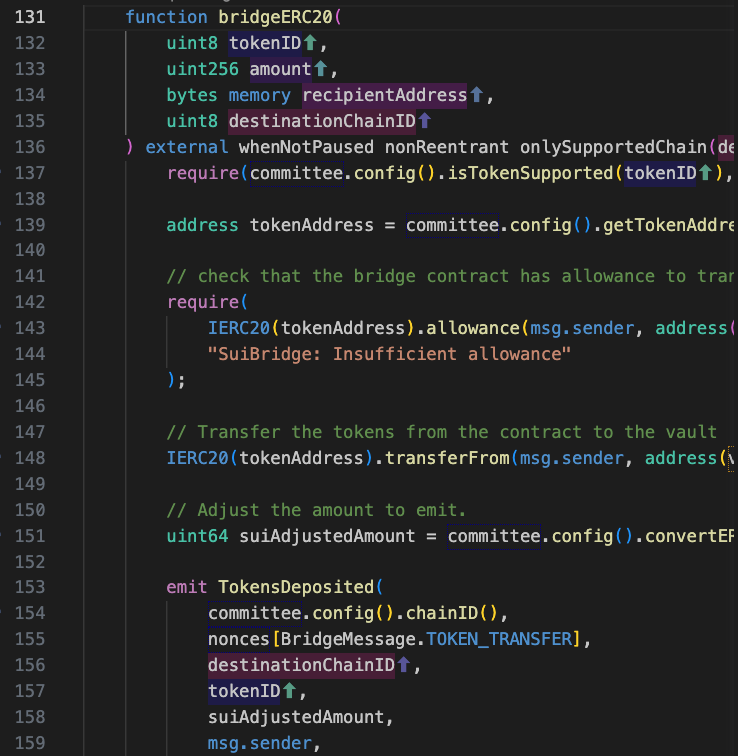
The function bridgeERC20() allows users to deposit supported tokens to be bridged to a specified destination chain. Let’s delve into the code of bridgeERC20() as as shown in the following code snippet:
The protocol first verifies on line 137 whether the token being deposited is supported by the protocol. Then, on lines 142-145, it checks whether the bridge contract has an allowance to transfer the token. Next, on line 148, it calls token.transferFrom() to transfer the tokens from the user to the vault. Subsequently, on line 151, it converts the amount of tokens based on their precision on the Sui chain. Finally, it emits a log, facilitating the Committee of Sui validators to verify and process the cross-chain bridge messages. Tokens such as Sui, WBTC, WETH, USDC, and USDT can all be deposited using this function call.
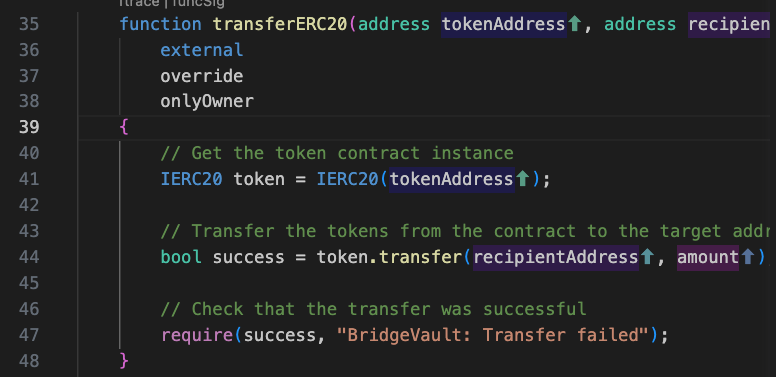
If a user transfers assets cross-chain from the Sui chain to the Ethereum (ETH) chain, they can use the transferBridgedTokensWithSignatures() function to move tokens to a specified receiving address. If the tokens are ERC20, the protocol will invoke the vault.transferERC20() function to transfer the tokens from the vault to the target address. Let’s take a look at the vault.transferERC20() function as described in the following code snippet.
In the function, the protocol first obtains the token address at line 41. Then, it calls token.transfer() at line 44 to transfer the tokens to the target address, returning a boolean value. Finally, at line 47, the protocol checks that this boolean value must be true.
As we previously analyzed, for tokens like USDT, there is no return value upon successful transfer. Consequently, if USDT is being extracted from the protocol, token.transfer() will return void, resulting in a failed execution. Consequently, USDT cannot be withdrawn from the protocol, and there is no function within the protocol to extract funds, leading to the permanent freezing of funds within the protocol.
Regarding such issues, OpenZeppelin[5] has already addressed and developed a library named safeERC20 to mitigate this problem. Therefore, it is recommended to utilize OpenZeppelin’s safeTransfer() function for withdrawing cross-chain funds.
** Timeline & Mitigation
On April 1st, the MoveBit team discovered a vulnerability related to asset freezing and promptly submitted it to Sui via the HackenProof platform
On April 17th, we submitted another vulnerability.
On April 19th, following communication between the Mysten team and engineers, both issues were confirmed.
On May 10th, this issue was resolved.https://github.com/MystenLabs/sui/commit/d01026e2f8c9128ff29f52811b507df745c38a86
** Reference:
2.https://about.google/appsecurity/
